Why Xcitium Does Not Have Same Problem as Crowdstrike ? In endpoint protection agent release cycle, the focus should be on stability, security, and minimizing disruptions. The cycle should begin with a thorough planning phase where up...
Latest Posts
The Update Trap: How Cybersecurity Vendors Risk Your Operations ? Recently, CrowdStrike experienced a significant issue causing widespread Blue Screen of Death (BSOD) incidents on Windows computers running its software. The company ac...
The world has witnessed another large-scale cyber-attack. On July 2, 2021, Kaseya, an IT Systems Management software firm, disclosed a security incident impacting their on-premises version of Kaseya's Virtual System Administrato...
Following the attack on FireEye, the details are revealed and the US Department of Homeland Security (DHS) has issued an Emergency Directive (ED) regarding a backdoor being exploited in SolarWinds Orion products. Several victims have...
First, consider a few definitions and terminologies before we proceed: Threat Actor: A threat actor or malicious actor is a person, entity, or object responsible for an event or incident that impacts, or has the potential to impact,...
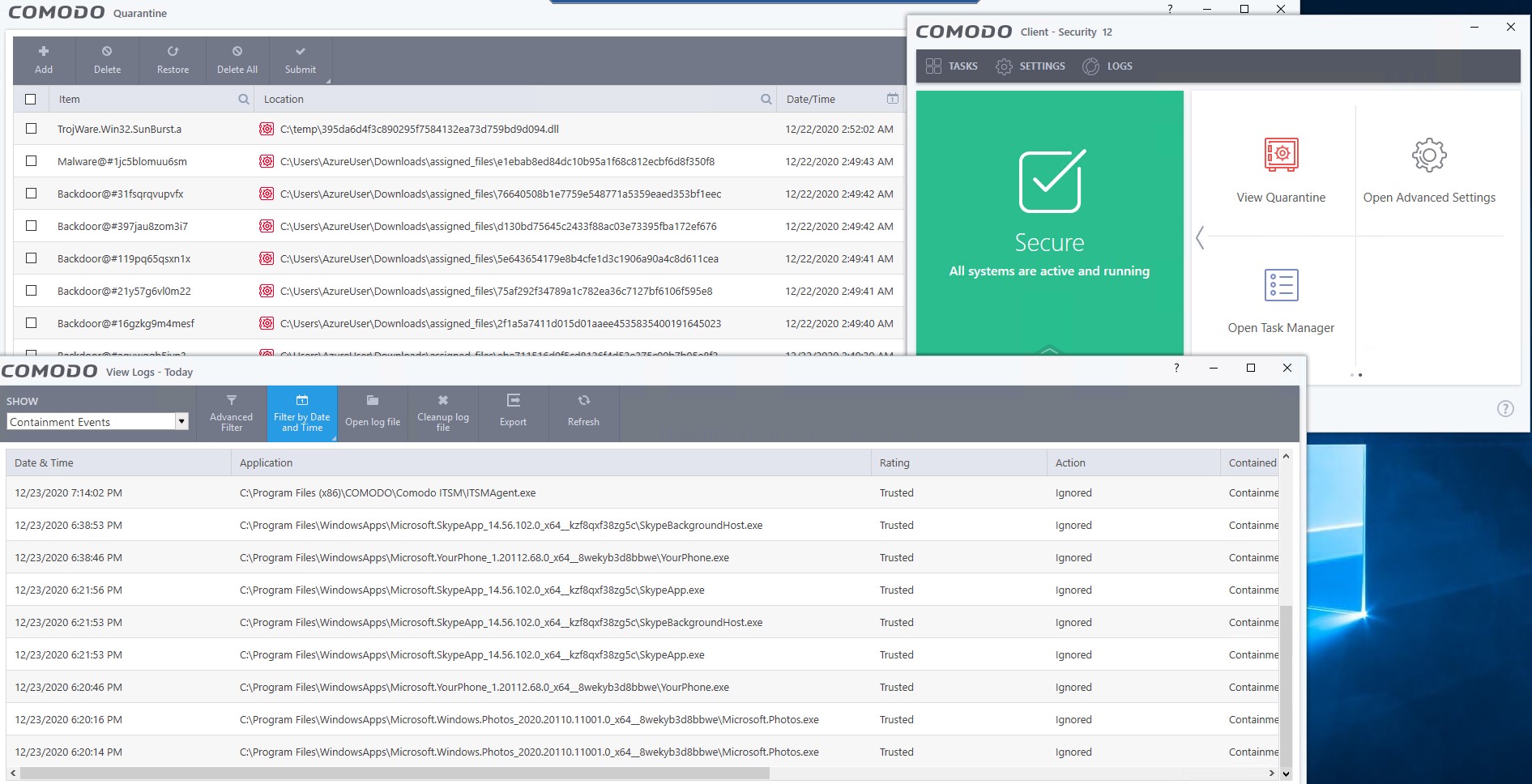
This post describes the architecture of Open EDR components. The documentation for a component usually includes an information which is enough for understanding how it works and for developing it. However, these documents don’t...
Xcitium was one of the pioneers of Extended Detection and Response into network (XDR), web and cloud and I guess I am the one to blame as I charted and executed the strategy for this in 2017. A few months later, starting seeing oth...
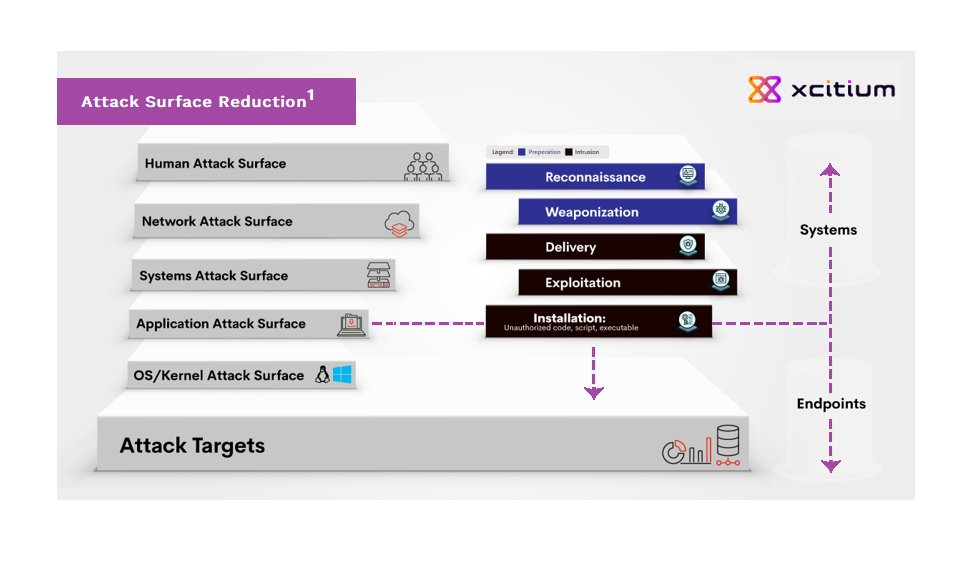
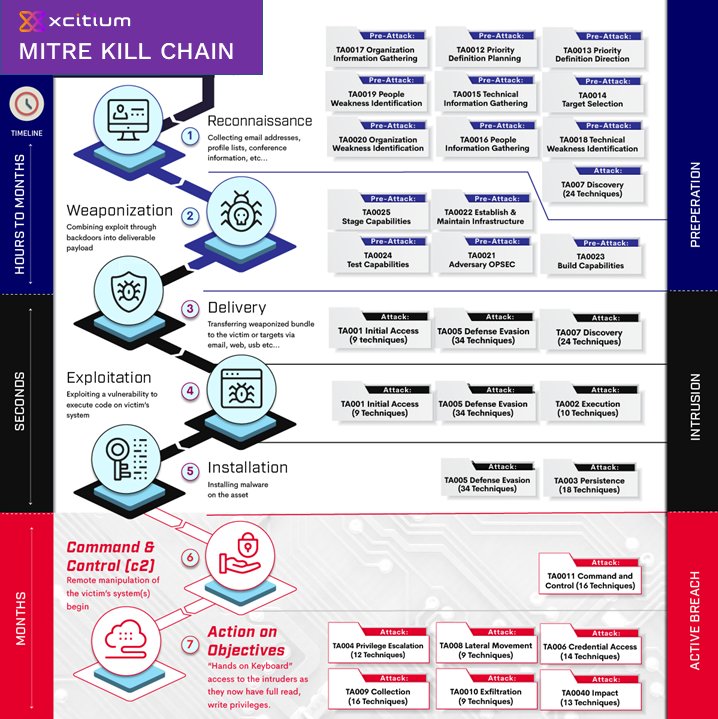
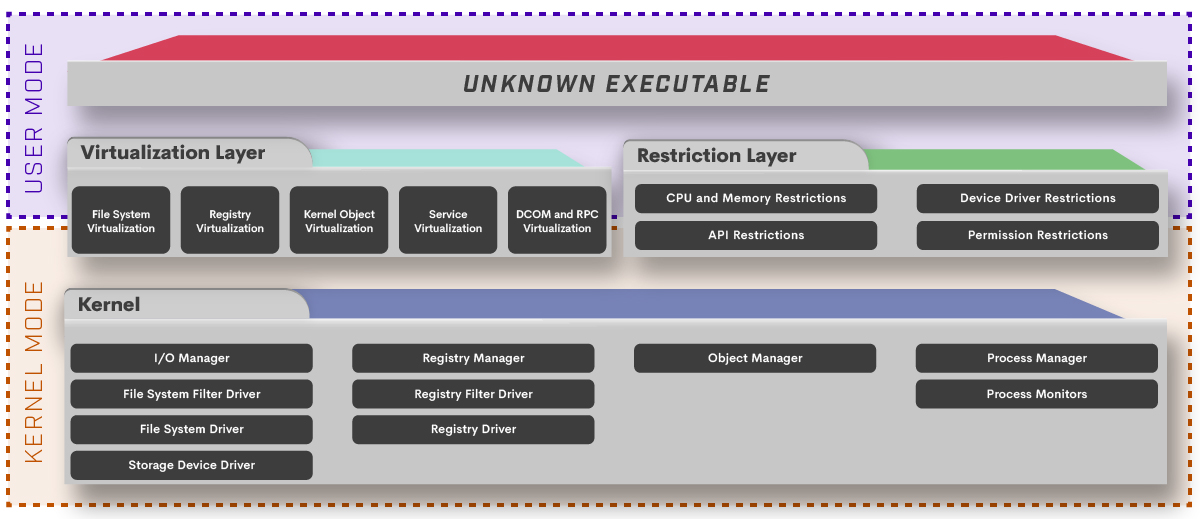
Endpoint Protection Kernel API Virtualization The Cyber Intrusion Kill Chain, aka Kill Chain, was adapted from military concepts. Lockheed Martin’s engineers were the first to apply it to cyber security attack stages. The core fra...
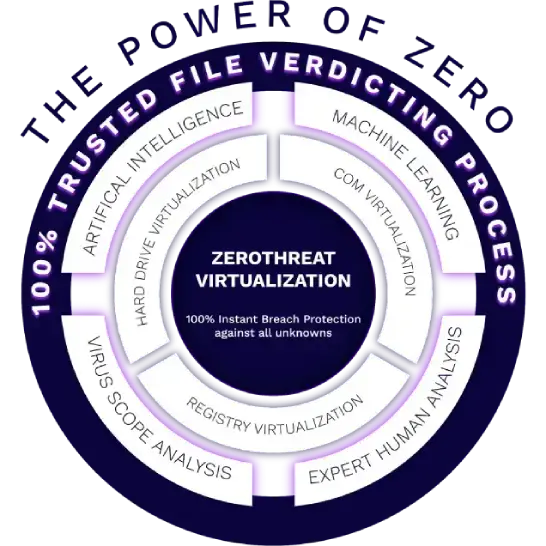
When it comes to securing your enterprise endpoints, it's important to have a foundational understanding that there are three types of files: the good, the bad and the unknown. Approaches such as Antivirus (both vendor-branded "next ...